SCADA stands for Supervisory Control and Data Acquisition but it is a term often used for data collection and presentation.
What is SCADA ?
SCADA is normally a software package designed to display information, log data and show alarms.
This can be graphical and tabular and can involve words and pictures (or mimics).
The software would normally be installed on a computer and all the various signals would be wired back to the central point (CPU), or marshalled and gathered using some form of bus system or direct wired.
SCADA can be used to monitor and control plant or equipment. The control may be automatic, or initiated by operator commands. The data acquisition is accomplished firstly by the RTU’s (remote Terminal Units).
The central host will scan the RTU’s or the RTU’s will report in Data can be of three main types.
Analogue data (i.e. real numbers) will be trended (ie placed in graphs). Digital data (on/off) may have alarms attached to one state or the other. Pulse data (e.g. counting revolutions of a meter) is normally accumulated or counted
Supervisory control and data acquisition – SCADA refers to ICS (industrial control systems) used to control infrastructure processes (Utilities, water treatment, wastewater treatment, gas pipelines, wind farms, etc), facility-based processes (airports, space stations, ships, etc,) or industrial processes (production, manufacturing, refining, power generation, etc).
The following subsystems are usually present in SCADA systems:
- The apparatus used by a human operator; all the processed data are presented to the operator
- A supervisory system that gathers all the required data about the process
- Remote Terminal Units (RTUs) connected to the sensors of the process, which helps to convert the sensor signals to the digital data and send the data to supervisory stream.
- Programmable Logic Controller (PLCs) used as field devices
- Communication infrastructure connects the Remote Terminal Units to supervisory system.
Generally, a SCADA system does not control the processes in real time – it usually refers to the system that coordinates the processes in real time.
SCADA Systems Concepts
SCADA refers to the centralized systems that control and monitor the entire sites, or they are the complex systems spread out over large areas.
Nearly all the control actions are automatically performed by the remote terminal units (RTUs) or by the programmable logic controllers (PLCs).
The restrictions to the host control functions are supervisory level intervention or basic overriding.
For example, the PLC (in an industrial process) controls the flow of cooling water, the SCADA system allows any changes related to the alarm conditions and set points for the flow (such as high temperature, loss of flow, etc) to be recorded and displayed.
Data acquisition starts at the PLC or RTU level, which includes the equipment status reports, and meter readings. Data is then formatted in such way that the operator of the control room can make the supervisory decisions to override or adjust normal PLC (RTU) controls, by using the HMI.
SCADA systems mostly implement the distributed databases known as tag databases, containing data elements called points or tags. A point is a single output or input value controlled or monitored by the system. Points are either ‘soft’ or ‘hard’.
The actual output or input of a system is represented by a hard point, whereas the soft point is a result of different math and logic operations applied to other points.
These points are usually stored as timestamp-value pairs. Series of the timestamp-value pairs gives history of the particular point.
Storing additional metadata with the tags is common (these additional data can include comments on the design time, alarm information, path to the field device or the PLC register).
Human Machine Interface
The HMI, or Human Machine Interface, is an apparatus that gives the processed data to the human operator. A human operator uses HMI to control processes.
The HMI is linked to the SCADA system’s databases, to provide the diagnostic data, management information and trending information such as logistic information, detailed schematics for a certain machine or sensor, maintenance procedures and troubleshooting guides.
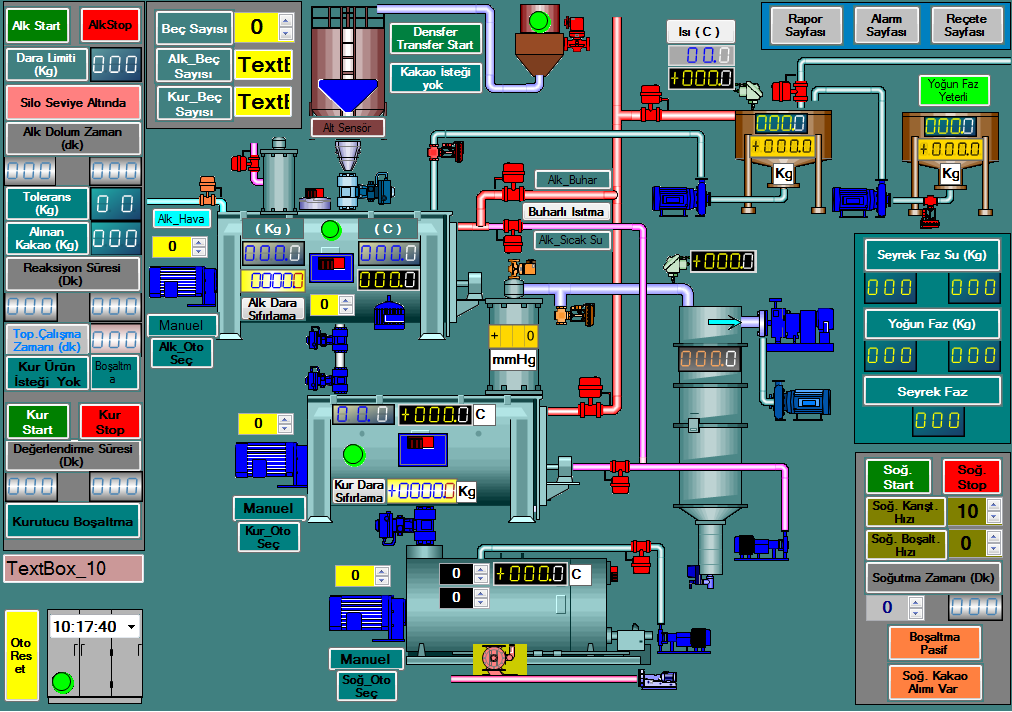
The information provided by the HMI to the operating personnel is graphical, in the form of mimic diagrams.
This means the schematic representation of the plant that is being controlled is available to the operator.
For example, the picture of the pump that is connected to the pipe shows that this pump is running and it also shows the amount of fluid pumping through the pipe at the particular moment.
The pump can then be switched off by the operator. The software of the HMI shows the decrease in the flow rate of fluid in the pipe in the real time.
Mimic diagrams either consist of digital photographs of process equipment with animated symbols, or schematic symbols and line graphics that represent various process elements.
HMI package of the SCADA systems consist of a drawing program used by the system maintenance personnel or operators to change the representation of these points in the interface.
These representations can be as simple as on-screen traffic light that represents the state of the actual traffic light in the area, or complex, like the multi-projector display that represents the position of all the trains on railway or elevators in skyscraper.
SCADA systems are commonly used in alarm systems. The alarm has only two digital status points with values ALARM or NORMAL. When the requirements of the Alarm are met, the activation will start.
For example, when the fuel tank of a car is empty, the alarm is activated and the light signal is on. To alert the SCADA operators and managers, text messages and emails are sent along with alarm activation.
SCADA Hardware
SCADA system may have the components of the Distributed Control System. Execution of easy logic processes without involving the master computer is possible because ‘smart’ PLCs or RTUs.IEC61131-39(Ladder Logic) is used, (this is a functional block programming language, commonly used in creating programs running on PLCs and RTUs.)
IEC 61131-3 has very few training requirements, unlike procedural languages like FORTRAN and C programming language.
The SCADA system engineers can perform implementation and design of programs being executed on PLC or RTU. The compact controller, Programmable automation controller (PAC), combines the capabilities and features of a PC-based control system with a typical PLC.
’Distributed RTUs’, in various electrical substation SCADA applications, use station computers or information processors for communicating with PACs, protective relays, and other I/O devices.
Almost all big PLC manufacturers offer integrated HMI/SCADA systems, since 1998.
Many of them are using non-proprietary and open communication protocols. Many skilled third party HMI/SCADA packages have stepped into the market, offering in-built compatibility with several major PLCs, which allows electrical engineers, mechanical engineers or technicians to configure HMIs on their own, without requiring software-developer-written custom-made program.
Remote Terminal Unit (RTU)
The RTU is connected to the physical equipment. Often, the RTU converts all electrical signals coming from the equipment into digital values like the status- open/closed – from a valve or switch, or the measurements like flow, pressure, current or voltage.
By converting and sending the electrical signals to the equipment, RTU may control the equipment, like closing or opening a valve or a switch, or setting the speed of the pump.
Supervisory Station
A ‘supervisory Station’ refers to the software and servers responsible for communication with the field equipment (PLCs, RTUs etc), and after that, to HMI software running on the workstations in the control room, or somewhere else.
A master station can be composed of only one PC (in small SCADA systems). Master station can have multiple servers, disaster recovery sites and distributed software applications in larger SCADA systems.
For increasing the system integrity, multiple servers are occasionally configured in hot-standby or dual-redundant formation, providing monitoring and continuous control during server failures.
SCADA Operational Philosophy
The costs resulting from control system failures are very high. Even lives may be lost. For a few SCADA systems, hardware is ruggedized, to withstand temperature, voltage and vibration extremes, and reliability is increased, in many critical installations, by including communications channels and redundant hardware.
A part which is failing can be identified and the functionality taken over automatically through backup hardware. It can be replaced without any interruption of the process.
Communication Methods and Infrastructure
SCADA systems initially used modem connections or combinations of direct and radio serial to meet communication requirements, even though IP and Ethernet over SONET/SDH can also be used at larger sites like power stations and railways. The monitoring function or remote management of the SCADA system is called telemetry.
SCADA protocols have been designed to be extremely compact and to send information to the master station only when the RTU is polled by the master station. Typically, the legacy of SCADA protocols consists of Conitel, Profibus, Modbus RTU and RP-570.
These protocols of communication are specifically SCADA-vendor. Standard protocols are IEC 61850, DNP3 and IEC 60870-5-101 or 104. These protocols are recognized and standardized by all big SCADA vendors. Several of these protocols have extensions for operating through the TCP/IP.
The development of many automatic controller devices and RTUs had started before the advent of industry standards for the interoperability.
For better communication between different software and hardware, PLE for Process Control is a widely accepted solution that allows communication between the devices that originally weren’t intended to be part of the industrial network.
Monolithic: The First Generation
SCADA Architectures
In the first generation, mainframe systems were used for computing. At the time SCADA was developed, networks did not exist.
Therefore, the SCADA systems did not have any connectivity to other systems, meaning they were independent systems. Later on, RTU vendors designed the Wide Area Networks that helped in communication with RTU.
The usage of communication protocols at that time was proprietary. If the mainframe system failed, there was a back-up mainframe, connected at the bus level.
Distributed: The Second Generation
The information between multiple stations was shared in real time through LAN and the processing was distributed between various multiple stations.
The cost and size of the stations were reduced in comparison to the ones used in the first generation. The protocols used for the networks were still proprietary, which caused many security issues for SCADA systems.
Due to the proprietary nature of the protocols, very few people actually knew how secure the SCADA installation was.
Modern SCADA Systems
Modern SCADA systems allow real-time data from the plant floor to be accessed from anywhere in the world. This access to real-time information allows governments, businesses, and individuals to make data-driven decisions about how to improve their processes. Without SCADA software, it would be extremely difficult if not impossible to gather sufficient data for consistently well-informed decisions.
Also, most modern SCADA designer applications have rapid application development (RAD) capabilities that allow users to design applications relatively easily, even if they don’t have extensive knowledge of software development.
The introduction of modern IT standards and practices such as SQL and web-based applications into SCADA software has greatly improved the efficiency, security, productivity, and reliability of SCADA systems.
SCADA software that utilizes the power of SQL databases provides huge advantages over antiquated SCADA software. One big advantage of using SQL databases with a SCADA system is that it makes it easier to integrate into existing MES and ERP systems, allowing data to flow seamlessly through an entire organization.
Historical data from a SCADA system can also be logged in a SQL database, which allows for easier data analysis through data trending.
Networked: The Third Generation
The SCADA system used today belong to this generation. The communication between the system and the master station is done through the WAN protocols like the Internet Protocols (IP).
Since the standard protocols used and the networked SCADA systems can be accessed through the internet, the vulnerability of the system is increased.
However, the usage of security techniques and standard protocols means that security improvements can be applied in SCADA systems.
SCADA Trends
In the late 1990s instead of using the RS-485, manufacturers used open message structures like Modbus ASCII and Modbus RTU (both developed by Modicon). By 2000, almost all I O makers offered fully open interfacing like Modbus TCP instead of the IP and Ethernet.
SCADA systems are now in line with the standard networking technologies. The old proprietary standards are being replaced by the TCP/IP and Ethernet protocols. However, due to certain characteristics of frame-based network communication technology, Ethernet networks have been accepted by the majority of markets for HMI SCADA.
The ‘Next Generation’ protocols using XML web services and other modern web technologies, make themselves more IT supportable. A few examples of these protocols include Wonderware’s SuiteLink, GE Fanuc’s Proficy, I Gear’s Data Transport Utility, Rockwell Automation’s FactoryTalk and OPC-UA.
Some vendors have started offering application-specific SCADA systems that are hosted on remote platforms all over the Internet. Hence, there is no need to install systems at the user-end facility. Major concerns are related to the Internet connection reliability, security and latency.
The SCADA systems are becoming omnipresent day by day. However, there are still some security issues.
SCADA Security Issues
Security of SCADA-based systems is being questioned, as they are potential targets to cyberterrorism/cyberwarfare attacks.
There is an erroneous belief that SCADA networks are safe enough because they are secured physically. It is also wrongly believed that SCADA networks are safe enough because they are disconnected from the Internet.
SCADA systems also are used for monitoring and controlling physical processes, like distribution of water, traffic lights, electricity transmissions, gas transportation and oil pipelines and other systems used in the modern society. Security is extremely important because destruction of the systems would have very bad consequences.
There are two major threats. The first one is unauthorized access to software, be it human access or intentionally induced changes, virus infections or other problems that can affect the control host machine. The second threat is related to the packet access to network segments that host SCADA devices.
In numerous cases, there remains less or no security on actual packet control protocol; therefore, any person sending packets to SCADA device is in position to control it.
Often, SCADA users infer that VPN is sufficient protection, and remain oblivious to the fact that physical access to network switches and jacks related to SCADA provides the capacity to bypass the security on control software and control SCADA networks.
SCADA vendors are addressing these risks by developing specialized industrial VPN and firewall solutions for SCADA networks that are based on TCP/IP. Also, white-listing solutions have been implemented due to their ability to prevent unauthorized application changes.
APPLICATIONS OF SCADA:
1)Application In Power Plants:
A group of Hydro and Gas generation plants when the load demand exceeds the generating capacity, These plants are considered as peak load plants because these plants can start in no time and deliver power to the grid.
These plants are located in the romote locations. These plants are controlled by opening and closing the valves of turbines so that they can deliver the power in peak conditions and can be kept on standby during normal load conditions.
2)Application In Oil & Gas Plants:
Many process control parameters, motors, pumps, valves are spread over the wide area in the field.
Control and monitoring applications include turning on and off motors, pumps, valves and gathering information of process parameters(like flow rate, pressure, temperature) continuously and taking certain decisions can be done through SCADA systems.
3)Applications In Pipelines:
Pipelines carrying oil, gas, chemicals and water which are located at varying distances from the plant needs continuous monitoring and control.
Control includes opening and closing the valves, starting and stopping the pumps. Monitoring the flowrate and other parameters to avoid leakage in the pipelines by acquiring the data and carrying out suitable controls is done through SCADA systems.
4)Applications In Power Transmission:
Electrical power transmission which is spread over thousands of kilometers can be controlled by opening and closing the circuit breakers and other functions, This is done in master control substation which can control the other substations through SCADA systems.
5)Applications In Irrigation Systems:
Irrigation systems which are spread over wide area can be controlled by closing and opening the valves, gathering the meter values of amount of water supplied and taking the control actions can be done through SCADA systems.
Arcticle Source : Inst Tools
Image Source : Inst Tools